If you have ASP.NET website on internet, you must make sure to implement following cofiguration steps to secure your website.
Block libwww-perl attack in ASP.NET Application hosted in IIS – Follow this article to configure this.
Some response headers reveal technical details about the server which must be removed. For example a sample response from an ASP.Net application may look like this
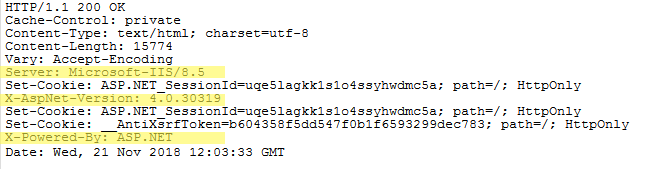
In this response “Server”, “X-AspNet-Version”, “X-Powered-By” headers are revealing technical details about the server. We can remove these unnecessary IIS response headers as following
Remove “X-Powered-By” Header – Open web.config and check for customHeaders tag. If this is not already there, then add it as child of “<httpProtocol>” and add “remove” entry for X-Powered-By as shown below
<configuration>
<system.webServer>
<httpProtocol>
<customHeaders>
<remove name="X-Powered-By" />
</customHeaders>
</httpProtocol>
</system.webServer>
</configuration>
You should also check the response from your Asp.Net application if this is using a shared hosting which may add additional server specific information to response headers. Add remove entry for all such headers in your web.config.
Remove “X-AspNet-Version” Header – In web.config file look for <httpRuntime> under <system.web>. Add enableVersionHeader attribute and set its value to false.
<httpRuntime targetFramework="4.5" enableVersionHeader="false" />
Remove “Server” Header – Add following line in Application_BeginRequest method of Global.asax.cs
protected void Application_BeginRequest(object sender, EventArgs e)
{
HttpContext.Current.Response.Headers.Remove("Server");
}
Add Security Headers in Response – Add additional security headers (X-Content-Type-Options, X-Frame-Options, X-XSS-Protection) in response to harden security of the application. Add entries in web.config as following
<customHeaders>
<remove name="X-Powered-By" />
<add name="X-Frame-Options" value="DENY" />
<add name="X-XSS-Protection" value="1; mode=block" />
<add name="X-Content-Type-Options" value="nosniff " />
</customHeaders>
If you are using iFrames in your website, you can set value of “X-Frame-Options” to “SAMEORIGIN”.
After implementing these, check the response headers in browser developer console of your liking. You can also use a third-party service such as https://securityheaders.com to quickly check whether or not security headers are returned correctly from your website. The scan may propose additional security headers for your website which you can implement if need be.
